This article is written by Aryashree Kunhambu, pursuing Diploma in Cyber Law, FinTech Regulations, and Technology Contracts from LawSikho.
Table of Contents
Introduction
The fight against terrorism and terrorist groups is a multi-front war in which all countries have to put up a united front. Over the years, various nations have identified the significance of funding in terrorist activities. Financing enables terrorism by helping terrorist associations to secure weapons, train forces and execute violent attacks. Even though there are diverse ideologies, capacities and opportunities amongst different terror groups, the infrastructural model used by most are similar in this regard.
Counterterrorism efforts of several states, particularly the subfield of counterterrorism finance (CTF), essentially focus on tracking the flow of funds through accounts maintained in registered financial institutions and preventing terrorist access to these funds. Such strategies and monitoring activities by intelligence bureaus and security departments of governments have reduced terrorist access to fiat currencies. However, due to this accomplishment, terror bands have discovered alternative technologies such as crypto-assets, with a decentralised and unregulated approach, to finance their activities.
In this article, I have examined why crypto-assets are susceptible to and can facilitate terrorism and how regulators have responded to these perceived threats.
What are crypto assets?
Crypto-assets are digital representations of value or contractual rights that use blockchain, a distributed ledger technology (DLT) and cryptographic hashing functions to secure transactional data. These assets can be stored and traded electronically. They work as a medium of exchange operating over a peer-to-peer lending platform using strong cryptography to verify the transfer of asset ownership and control the creation of additional coins and tokens. Crypto assets can also be an investment and used to access goods and services. Today, the market provides several crypto-assets in currencies or tokens, known by several names such as Bitcoin, Ripple, Dogecoin, Ethereum, Litecoin etc. The appeal of such new technology has piqued the interest of several users however, in reality, without any regulatory authority involved, any loss of asset cannot be legally recovered.
Criminal exploitation of crypto-assets
Crypto transactions take place across the globe without the intervention of any central regulatory authority or foreign exchange commissions. The central bank and the securities exchange board of a country generally regulate currency exchanges and investments within their jurisdiction, but such measures do not apply to crypto-asset transactions. Two principal concerns raised due to the nature of such transactions are-
- The possibility of violation of foreign exchange laws due to the lack of a central regulatory body. For example – Bitcoin transactions take place through Bitcoin “wallets” over Bitcoin “exchanges”, but there is no regulator present to monitor such transactions.
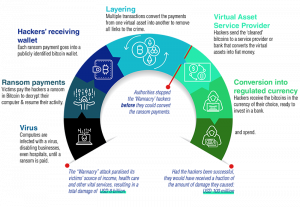
- Money laundering and terror financing are other highlighted aspects as proceeds from criminal activity are shown as legal money with no system to verify how a person purchasing a Bitcoin has earned that money. Anonymous/ pseudonymous systems in such peer-to-peer operating platforms could subject the users to unintentional breaches of Anti-Money Laundering (AML), Combating of Financing of Terrorism (CFT) laws due to the absence of information of counterparties.
On June 11th, a show-cause notice was sent to WazirX by the Enforcement Directorate (ED) of India, claiming that the said crypto exchange platform did not collect the required documents under the AML/CFT norms and FEMA guidelines, thus in clear violation of these laws. The incoming amount received by the platform was worth Rs. 880 crore from Binance accounts, while Rs. 1,400 crore worth of cryptocurrency was returned. The obstacle faced by the investigation agency was that none of those transactions was available on the blockchain for an audit or investigation.
Nature of crypto assets
The technology behind crypto-assets is complex. Nuanced and sophisticated digital assets provide high-level privacy and the potential to use and transfer currency offline, which disables law enforcement agencies to trace illicit transactions. In this regard, it becomes critical to understand the properties of crypto-assets that enable terror financing plots to facilitate activities such as fundraising for attacks and operations, illegal drugs and arms trafficking, remittance and transfer of monetary funds.
-
Anonymity
Virtual currency systems on the Internet have non-face-to-face customer relationships and may permit anonymous funding through unverified sources. For example, Bitcoin addresses by design have no central server or service provider and operate with accounts with no names or other customer identification systems. These currencies commonly rely on complex infrastructures that involve several entities, often spread across several countries, to transfer funds or execute payments making it less likely to be detected. Recent techniques built into some newer applications such as “coin mixing” hide ownership or obfuscate IP addresses that make identification more difficult.
The military wing of Hamas, Izz ad-Din al-Qassam Brigades (AQB), a designated terrorist organization, collected money through a website that generated a new Bitcoin address for every new donor. This is the first verified example of such technology deployed by a terrorist organization in 2019. It even published a video on its website, instructing people how to donate anonymously using public Wi-Fi, so the computer IP address could not be identified by law enforcement. Thus, anonymity plays a big role in fundraising activities for terrorist organisations.
-
Usability
Cryptocurrencies are not very easy to use by nature and are more appealing to technically adept persons. Anonymous management of crypto-assets requires more technical sophistication, but rising trends indicate that the technical ability of both users and the public, in general, is increasing. Cryptocurrency developers are enhancing usability and making these systems more secure. Today, virtual currency systems can be accessed via the Internet on any device and can be used to make cross-border payments and fund transfers. It plays a pivotal role in terror financing as third parties from any country who support the ideologies of the terrorist organisation can use these platforms to fund their propaganda.
-
Security
The degree to which the cryptocurrency infrastructure secures the confidentiality, integrity, and accuracy of transactions and user accounts determines how secure the system is. Many formerly run crypto exchanges allowed users to create online wallets which were compromised. Alternatively, user-controlled wallets and hardware wallets that use dedicated devices to store currencies have developed to provide safer storage spaces. For remittance and transfer of funds by terrorist organisations, security is essential as large amounts of funds are vulnerable to theft or detection.
-
Acceptance
As the popularity of crypto-assets spreads across the world, the number of crypto users increases. Initially, crypto-assets had a limited reach, but this narrative has significantly changed over the years. The future trajectory of these currency technologies is only growing at a fast pace which makes use by terrorists more plausible. Today, many Bitcoin ATMs and Bitcoin exchanges are present in countries that have seen multiple foreign fighters join ISIS in the Middle East and have an increased risk of terror attacks.
-
Reliability
Price stability supports trust among transaction partners and ensures budgetary consistency in the face of unstable prices. Reliability is the speed and availability of transactions to users. It is crucial to terrorist organisations as in some situations, transfer of funds to support attacks may be time-sensitive and may fail if prices are unstable (particularly exchange rates with fiat currencies).
-
Volume
In the cryptocurrency infrastructure, volume refers to the time-averaged aggregate size of transactions. Such transactional volume is a hindrance to reliable transfer. The low volume makes the price more sensitive to transactions and makes the transfer of large amounts of money more expensive. The value of the currency increases when it is purchased and drops again when it is sold later. Cryptocurrency can support and hide large-scale transactions that enable deep-pocketed donors to make sizable donations to terrorist organisations.
Some of the factors that would discourage the use of crypto-assets by terror groups, in particular, would include:
- Continued instability and infighting in the cryptocurrency community.
- Cooperation between international law enforcement agencies and intelligence.
- Developments in legislation and law enforcement.
Global regulatory response to terror financing through crypto-assets
A few notable achievements on the part of global anti-terrorism efforts are as follows:
- Japan requires entities to register as a Crypto Asset Exchange Provider to carry out exchange services. The law protects customers of such service providers and combats money laundering and financing terrorism simultaneously.
- Interpol’s international anti-cybercrime centre in Singapore has created its cryptocurrency to fight crime involving digital currencies like Bitcoin. Interpol is also a partner in the European-Union funded Project TITANIUM and has assisted in developing a blockchain analytics tool called GraphSense that supports the tracing of cryptocurrency transactions. It can search for cryptocurrency addresses, tags and transactions that facilitate ‘follow the money’ strategies by identifying clusters related to an address.
- The Financial Crimes Enforcement Network (FinCEN) of the United States has issued guidelines that included virtual currencies within the ambit of its regulations.
- In Germany, the general financial regulatory regime brings various DLT tokens within the financial services, the ambit of banking, capital markets, anti-money laundering (AML) and other laws. The monetary regulatory authority (BaFin) efficiently included digital currencies like Bitcoin within the general financial services licensing scheme.
- Canada enacted the Proceeds of Crime (Money Laundering) and Terrorist Financing Act in 2019 (the Regulation). Recent amendments to the regulation include dealers in virtual currency and foreign money services businesses (MSBs) that service customers in Canada.
FATF report recommendations on crypto-assets
The Financial Action Task Force (FATF) founded in 1989, is an inter-governmental body that sets standards and promotes effective implementation of operational, legal and regulatory measures to uphold AML/CFT measures and combat other related threats to the integrity of the international financial system. The FATF recommendations to combat threats arising out of new technologies are as follows:
- Countries and financial institutions should identify and evaluate the risks that may arise due to the development of new technologies and products concerning money laundering or terrorist financing.
- Financial institutions should perform a risk assessment before the launch of the new products, business practices or the use of new or developing technologies to mitigate the risk involved.
- Countries should ensure that digital asset service providers adhere to AML/CFT laws and are licensed or registered. They must be subjected to effective systems for monitoring and ensuring compliance with the relevant measures called for in the FATF Recommendations.
The FATF also works to identify national-level vulnerabilities in collaboration with its international stakeholders to prevent misuse within nations. India along with the Asia Pacific Group of FATF will conduct a mutual evaluation of its anti-money laundering regime and legal measures to check financial crimes in 2021.
India’s AML/CTF regime
The AML/CFT regime in India is relatively young. The following legislative actions have been undertaken regarding the same:
- The Prevention of Money Laundering Act, 2002 (PMLA) came into force in 2005 and was subsequently amended in 2009.
- The Unlawful Activities (Prevention) Act, 1967 (amended in 2004, 2008 and 2012) criminalised terror financing as well as holding proceeds from terrorist activities. The scope of UAPA was broadened to include requirements of the United Nations Convention for the Suppression of the Financing of Terrorism (FT Convention).
- Individual laws that target illegal funding activities in India, such as the Foreign Exchange Management Act (1999), Prevention of Money Laundering Act (2002) and The Narcotic Drugs and Psychotropic Substances Act (1985) are also available.
While India has no regulatory framework to monitor crypto-assets, the Reserve Bank of India has issued a notification instructing banks as well as other entities dealing in virtual currencies to carry out customer due diligence processes in line with regulations governing standards for Know Your Customer (KYC), AML/CFT obligations of regulated entities under PMLA, 2002 in addition to ensuring compliance with relevant provisions under Foreign Exchange Management Act (FEMA) for overseas remittances.
It would be appropriate to include crypto-asset businesses within the Prevention of Money Laundering Act, 2002 as it is the definitive law of Know Your Customer/ Anti-Money Laundering (KYC/AML) in India. A risk-based approach can be taken to approach money laundering concerns while avoiding a complete prohibition on supporting such businesses. The following changes to the Act would go a long way:
- The PMLA regulates “reporting entities”, which includes banking companies, financial institutions, intermediaries or any person carrying on a designated business or profession. The phrase “person carrying on a designated business or profession” includes precious metals dealers, game operators, real estate agents etc. Crypto businesses must be included within this phrase as it would then include all such businesses within the framework of the PMLA, including the ‘Client Due Diligence’ requirements under Rule 9 of the Prevention of Money-Laundering (Maintenance of Records) Rules.
- The Reserve Bank of India, in any event, has the power under the Prevention of Money Laundering (Maintenance of Records) Rules to prescribe measures to verify a client’s identity, including information regarding his business relationships, nature and value of transactions and the type of client he is to determine money laundering and terrorist financing risks involved.
AML/CFT tools when included can provide the following benefits to entities dealing in virtual assets while creating a safe trading environment for their customers:
- Exposing the infrastructure of various organizations involved in criminal activities, channels of corruption, and plots to commit terror acts.
- Providing authorities with roadmaps to crackdown criminal and illicit activities.
- Recovery and forfeiture of unlawfully acquired assets.
- Providing support for broad and effective deterrence efforts while combating a wide range of criminal activities, including the financing of terrorism.
Conclusion
Terror financing has been a key concern for regulators and politicians alike. Oversight of crypto-assets must increase as the real advantages and disadvantages of these channels to terrorist organisations still lie in uncertainty. Lax and inconsistent regulations must be replaced with strategically formulated ones to target both the sender and receiver of funds through virtual currency markets. Focussing on measures to prevent the criminal exploitation of upcoming technologies will help governments to ensure that terrorist organisations will not be able to further their agendas as no adequate funding structures will be available for their use.
References
- https://www.globallegalinsights.com/practice-areas/blockchain-laws-and-regulations/japan#:~:text=In%20fact%2C%20Japan%20was%20the,%E2%80%9D
- https://www.forbes.com/sites/jnylander/2015/08/31/interpol-creates-digital-currency-to-fight-bitcoin-crimes/?sh=41739b89195d
- https://www.interpol.int/en/How-we-work/Innovation/Darknet-and-Cryptocurrencies
- https://thelawreviews.co.uk/title/the-virtual-currency-regulation-review/germany
Students of Lawsikho courses regularly produce writing assignments and work on practical exercises as a part of their coursework and develop themselves in real-life practical skills.
LawSikho has created a telegram group for exchanging legal knowledge, referrals, and various opportunities. You can click on this link and join:
 Serato DJ Crack 2025Serato DJ PRO Crack
Serato DJ Crack 2025Serato DJ PRO Crack











 Allow notifications
Allow notifications


