This article is written by Shrikar Ventrapragada pursuing a Diploma in Cyber Law, Fintech Regulations, and Technology Contracts from Lawsikho.com.
Table of Contents
Introduction
In recent days, in every newspaper we open, we hear about the cybersecurity breaches taking place in every other organisation. Even very well-known technology firms make sure that their cybersecurity defence is up-to-date in order to avoid any leakage of any sort of information irrespective of it being classified or non-classified information. Cyber defence can be defined as a mechanism that defends a computer network, which involves, swift response to breaches and creating a wall in the firm’s infrastructure which behaves as a protection layer and secures the delicate information owned by the firm/ organisations. Cybersecurity is not only used by IT firms and companies but it is even used by government entities and even by every possible private network.
The North Atlantic Treaty Organization (NATO) claims that the first instance of cyberwarfare was the Morris Worm incident. In 2010, the first-ever Digital Weapon namely ‘Stuxnet’, this weapon targeted a Nuclear Facility in Natanz, Iran. The attack was called ‘Operation Olympic Games’ and was claimed to be executed by Israel and the US jointly. The Stuxnet was an infected USB drive, which completely paralyzed the hardware and software facilities at the Nuclear facility. Stuxnet is claimed to be a computer worm that is used to control a factory’s assembly line. Cyber security’s main motive is not only to defend a network but it should also be equipped to prevent, scan and provide timely responses to any threat that may have been caused in the past and is still a threat to the organisation in the present and to prepare for future unexpected events. With the growing ambit of technology in recent days, there has also been an upgrade to cyber-attacks. The main aim of cyber defence is to protect sensitive details as well as to protect assets. 
What is the need for implementing the latest cyber technology?
Improvised targets
Cybercrimes are no longer considered petty crimes. They have increased equally alongside technology. Gone are the days when cyber-crimes were a bridge to extract a small amount of money from a person’s bank account. Cyber securities are now being used by top-notch government organisations such as Pentagon, which is considered to be the safest network, that is because of the increase in the threat of getting hacked by an anonymous person who later the government finds it hard to even track.
Advanced cyber threats
The main reason behind the advancement in cyber defence is mainly due to the advancement in cybercriminals. Cybercriminals have access to more advanced technology than any country’s government has ever imagined. Moreover, the increase in the knowledge about the dark web on the internet has made it possible for cybercriminals to go underground even before anyone notices them.
After-effects of a cyber attack
All the business activities are linked to a common network. In fact, nowadays all the business activities are done online, in a digital format, everything is dependent on the system and its networks. This makes it easier for breachers to access the critical data. Once the data has been breached, it points out a finger on the credibility of the company, due to which the whole goodwill of the firm or even a government is drastically affected.
In case of the data breach leaked by Facebook in 2018, it created havoc on social media, people started the #quitfacebook trend, which forced Facebook to make some critical changes in their privacy policy. It even affected the no. of users Facebook had before and they now have. One case of data breach led to questioning of all the social media platforms credibility, it questioned whether every platform is the same as Facebook. It made every individual think about whether even their personal data was being accessed by someone unknown?
Nature of cyber-attacks
Cyber-attacks are not only made on Governments or on internet websites, it is even possible to hack a power grid of a city. Which creates public inconvenience at large. It affects the revenues collected by the local municipal corporations. The system so damaged needs to be fixed, the charges to fix the whole power grid should be a massive expenditure for the state government. The impact of such cyber-attacks is no longer surrounded by an individual but they expand to the country’s economy and even the political systems.
Latest technologies for cyber defence
Humans created technology and hence it is a man who can get rid of the technology. There is no technology that cannot be defeated. Every time technology improves, there are people out there who aim to defeat this barricade. Hence, the best choice is to keep on adapting to changes that come our way. Here are a few most advanced technologies in the world:
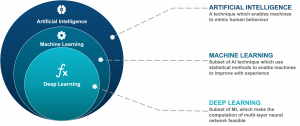
Artificial Intelligence (AI) and deep learning
AI is the most talked-about term in the country nowadays. AI can very well be used in the application of protection of Cyber defence. The best example of this kind of technology is Google. Whenever we try to log in to our google account on a new device, there is two-factor authentication. This authentication works by confirming the user’s identity on the basis of 2-3 different grounds. These grounds can be something they know, are and have.
Deep learning is a very in-depth concept of AI. Deep learning is used to verify the data. It keeps a record of all the transactions and even real-time communications in order to detect any virus or unwanted activities on your network.
Behavioural analytics
After the whole Facebook- Cambridge Scandal, a person is well aware of the data being misused for behavioural analysis. This technique is frequently used in social media platforms and online advertisements in order to get the right set of audience. But this type of technology is still under study and it is on the verge of being explored and developed for advanced cyber defence technologies. This method helps in ascertaining the pattern of a system and tracks the network activity, to instantly detect a real-time threat or possibility of a threat. For example, a certain user’s device indicates an abnormal increase in data transmission which could possibly be a cybersecurity breach. While this kind of technology is in most cases used for networks, its usage in applications and devices is still growing.
External hardware application
A password or a numbered pin is not efficient enough to protect our hardware from being corrupted. By the use of embedded authenticators, they are emerging to be one of the safest ways of verifying a user’s identity. World’s largest chip manufacturing company, Intel has introduced a 6th Gen vPro Chips. These chips are very powerful user authentication chips that are embedded into the hardware itself, hence requiring no usage of external drives. The company claims that these chips would change the structure of ‘Authentication Security’, the chips are built to work at multiple levels and methods of authentication working in tandem.
Blockchain cybersecurity
One of the latest cybersecurity technologies is growing dramatically and is getting the recognition it should. Blockchain technology works by determining the two parties to the transaction. This kind of cybersecurity works on the basis of peer-to-peer network fundamentals. Blockchain’s main focus is to create trust in a non-trusting ecosystem. Every participant of the blockchain is solely held responsible for the verification of the authenticity of the data provided. Blockchains create an impenetrable wall around the network which is just not possible to be breached and hence there are zero chances of any compromise. Blockchains usually create a robust verification system to keep potential cyber threats at bay. For example Mobilecoin
Zero-Trust Model
The name speaks for itself, under this model of cyber defence, it is already assumed that the network is pre-compromised. Hence the network can no longer be trusted, which forces a person to enhance the internal and external security on his/her network.
The main crux of this type of cybersecurity model is that it mandates a person to enhance the internal and external networks. Even before the network is compromised, it is assumed that it is already compromised which automatically means to provide the required protection. This also includes the need to identify a business’s critical data, tracking the flow of such data, segregating the logical and physical components, making sure that the policies of the firm are under constant check and are being updated from time to time.
Conclusion
In a country like India, there are close to 560 million users, which makes us the 2nd largest internet user. It is said that by the end of this year, due to the pandemic, this number is expected to reach 600 million users. But on the other side, these huge figures demand a huge need for vigorous cyber defence technologies. An article was published in the New York Times on 23rd Feb 2021, that said, US officials were not able to detect a cyber-attack for weeks, until a private cybersecurity firm namely, FireEye, alerted the American intelligence about the hackers that had invaded multiple layers of defences.
Though cybersecurity is developing day by day, hackers are also consistently upping their game and are looking for ways to get into a new system. In order to make sure that the cyber-crimes are reduced and the efforts of the fraudsters are gone in vain, we need to have certain laws in place and the law-makers need to predict the loopholes in cybersecurity and make laws accordingly. As the dependency of humans on technology is increasing, cyber laws in India as well as across the globe are in dire need of constant push and modifications. Moreover, due to the pandemic, everything has been changed to work-from-home modules. Cybercrimes can be brought under control only if the lawmakers of the society and network provider work in correspondence with each other.
References
Students of Lawsikho courses regularly produce writing assignments and work on practical exercises as a part of their coursework and develop themselves in real-life practical skills.
LawSikho has created a telegram group for exchanging legal knowledge, referrals, and various opportunities. You can click on this link and join:
 Serato DJ Crack 2025Serato DJ PRO Crack
Serato DJ Crack 2025Serato DJ PRO Crack










 Allow notifications
Allow notifications


