This article is written by Jyotiranjan Mallick, pursuing a Diploma in Cyber Law, FinTech Regulations, and Technology Contracts from LawSikho.
Table of Contents
Introduction
The covid pandemic resulted in a mass disruption of the entire global system in terms of economy, health services, and industries. The pandemic stalled decades of development and businesses creating an environment resulting in the quarantine of millions of people in their homes. The pandemic also exposed the vulnerability of the health care regime which was nearly on the brink of collapse, effectively forcing the government to stall the liberties of citizens by imposing curfews. This also showed the dark side of cyber-attacks that are conducted to debilitate medical institutions for a number of purposes. Cyber-attacks have also targeted critical health infrastructure causing massive security failures for critical health information. Attacks on healthcare also cause direct harm to healthcare officials and patients. The cyber-attacks in the medical facilities have massive implications since it globally has a deep-rooted societal impact which poses dangers to health and human life.
The covid-19 has accelerated the rise of technologies in the health space in the form of digital health, the use of telehealth for consultation by the patients or using sophisticated technologies. In spite of the threat received from such instances of cyber-attacks, hospitals and health institutions have not upgraded themselves with technology or manpower to tackle the same. As many hospitals have failed to properly segment their networks, such an unsecured network is vulnerable and prone to cyber-attacks.
The cyber threat to medical institutions
Rapid cyber-attacks are evolving with the advancement of technologies. Although attacks on medical institutions aren’t a new phenomenon, however, the advent of covid 19 has resulted in an alarming level of such attacks. Vaccine research centres are easy targets of cyberespionage, hospitals are the prime targets where the central health database is hacked to be later recovered by paying bitcoin as ransom. Healthcare professionals and international health organisations are targeted with a blend of disinformation campaigns to dismantle government credibility. These are some of the prime methods with which health institutions are attacked with cyber malware.
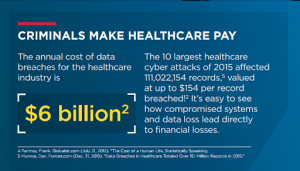
One of the primary sources of attack is ransomware which creates both short and long-lasting consequences. This specifically involves the fact that they may jeopardise the technical system that manages the digital health data of the patients. This data then can also be used to create a model for extortion resulting in increased cooperation among cybercriminals who have sought to maximize their profits.
The root cause for the threat to medical institutions from cyber-attacks is fragile digital infrastructure. Cybercriminals are exploiting the complex, vulnerable and sometimes outdated healthcare digital environments including medical devices and IT infrastructure. Although big hospitals and healthcare institutions have equipped themselves with sufficient tech and manpower to tackle such cyber-attacks however, most of the smaller and mid ranging health institution chains do not have the capacity to resist the same. This makes a large number of such institutions prone to cyber-attacks. The lack of a proper healthcare cybersecurity team is compounded by a lack of human resources to effectively tackle such problems by improving resilience and recovery.
What are the prime reasons that fuel cyber-attacks on medical institutions?
Attacks on healthcare are low-risk, high-reward crimes. Criminals and state actors are joining forces against healthcare with varying motives and agendas.
- Lucrative international business – Medical institutions are a hub of sensitive personal data related to health. The medical records of patients and the activities associated with hospitals and organizations have a high monetary value due to the risks being associated with the same. The healthcare sector represents a financial opportunity in the eyes of cyber threat actors. Healthcare data has a monetary value. While prices fluctuate, a medical record of a single individual can be sold for an average of USD 250 in the underground markets. The duty of secrecy provided by an institution to its customer and patients provides value to such data and cyber hackers play on this vulnerability.
- Geopolitical interests – Cyber-attacks on the critical infrastructure of an enemy nation serve as a hard tool for showing the cyber prowess of a nation. This has been significantly seen in recent days when cyber-attacks by China and Russia are being orchestrated to serve geopolitical interests and exert influence. State actors are especially targeting COVID19-related research and development – including data on vaccines and treatments – in an attempt to gain a competitive edge.
- Lack of reporting cyberattacks in medical institutions – As previously depicted, the reputation of a medical institution or organization depends upon the protection of sensitive personal data of the individuals. In the event of a cyber-attack, organizations tend to under-report such matters so as to protect the repute and resist from facing any legal troubles in terms of liabilities and prosecution.
How are cyber-attacks conducted on medical institutions?
- Disruptive attacks – attacks that use ransomware and malware pose serious repercussions to the digital health data of the individuals. This in turn affects the ability of a medical institution to provide medical facilities. The malware is launched to the central health database through various factors such as illegal download, activity from unauthorized sites etc. which ultimately results in system crashes and data theft. The covid pandemic resulted in the rapid insurgence of such activities where leaked data was used to claim ransom in terms of cryptocurrencies. While some parts of data stolen from these organisations are used to extort ransoms, a significant portion is also left for it to be auctioned creating a commercial racket of digital health data.
- Data breaches – the monetary value of sensitive medical data results in a number of data breaches. Data breaches can take place in terms of using computer malware, inducing viruses in the central health repository.
- Disinformation operations – healthcare organizations have been at the centre of cyber-enabled information operations, which comprise the exfiltration, manipulation, and dissemination of information. This was prominently observed during the covid pandemic when a number of misleading campaigns were led to spread rumours about aspects related to vaccines and their effects.
 What steps can be taken to protect healthcare institutions from cyber-attacks?
What steps can be taken to protect healthcare institutions from cyber-attacks?
Domestic law and jurisdiction are the first avenues to consider when discussing the healthcare context and attacks against hospitals and medical facilities. One of the prime methods can be attributed to strong actions by state and non-state actors to eliminate the proliferation of cyber-attacks in medical centres. State actors can contribute by framing a strong framework for dealing with cyber disputes while simultaneously resolving cross-border cyber-attacks through international resolutions. State actors should cooperate among themselves to form inter-party treaties to tackle legal immunity that is given to the operation of domestic laws to foreign citizens from where the cyber-attacks originated. To respond to and stop internationally conducted cyber-attacks under the principle of due diligence, state actors must take all feasible measures to prevent or stop an attack that emanates from its territory or infrastructure under its jurisdiction or control, as long as they are aware of it. The same principle should be applied to non-state actors, in which the private actors should be held accountable and must provide support in terms of tackling such cyber-attacks. This can be supported by uniform application of international laws for states to recognize, in a timely manner. Apart from the state and non-state actors, cyber-attacks can be prevented by taking proactive measures in terms of using updated security and defence against malware, equipping necessary human resources that are capable of dealing with such issues and using anti-virus for phishing. The EU, through GDPR, has made data security an integral part of law and India is taking strong steps to have robust data protection and data security law.
Conclusion
The threat of cyber-attacks has to be solved not only by the means of law and policies but also by proactive measures by medical institutions and organizations by equipping themselves with sufficient defence. There continues to be an outbreak of these attacks, further stressing the urgency of the matter at hand. Building the cyber resilience of a hospital is vital and it is a shared responsibility. This has to be achieved by creating awareness in the medical domain towards the field of digital safety, training all levels of staff members to take proactive measures to ensure the safety of the critical data of the patients, and considering the option of optimising the existing tools of cyber safety through more efficient systems. Users (i.e., clinicians and administration staff) should undergo training and should practice digital hygiene, decision-makers should enforce the proper policies and consider cybersecurity in purchasing decisions, and manufacturers should equip their products with the appropriate cybersecurity measures. The IT team of the hospitals and medical centres can solve a great deal of the problems by enforcing proper cyber-safe policies and employing counter theft measures such as auto-checking suspicious URLs in e-mails for linked malicious code, whitelisting trustworthy websites and applications, as well as blocking Flash, advertisements and untrusted JAVA code on the Internet. Other manual techniques can be employed in the form of changing default passwords and regularly updating security configurations on laptops, servers, workstations, firewalls, etc. The importance of tuning the digital health data to appropriate legal standards of a nation must be kept in mind to avoid any repercussions in terms of the data breaches, this can be achieved by employing the latest standards of safety efficacy mechanisms reasonably prescribed in industrial standards.
Students of LawSikho courses regularly produce writing assignments and work on practical exercises as a part of their coursework and develop themselves in real-life practical skills.
LawSikho has created a telegram group for exchanging legal knowledge, referrals, and various opportunities. You can click on this link and join:
 Serato DJ Crack 2025Serato DJ PRO Crack
Serato DJ Crack 2025Serato DJ PRO Crack









 Allow notifications
Allow notifications


