This article has been written by Khushant Jolly, pursuing a Diploma in Cyber Law, FinTech Regulations and Technology Contracts from LawSikho.
Table of Contents
Introduction
The Central Government under the powers conferred to it by sections 69A(2), 79(2)(c) and 87 of the Information Technology Act and in supersession of the earlier Information Technology (Intermediary Guidelines) Rules 2011, has enacted the Information Technology (Guidelines for Intermediaries and Digital Media Ethics Code) Rules, 2021 (hereinafter the ‘Code’). The ‘Code’ includes guidelines meant to empower the users of social and digital media, over the top (OTT) media streaming platforms and online news sites, by holding those companies accountable for the content that is being circulated on their platforms. It provides a soft-touch oversight mechanism. We shall only be discussing the Guidelines for Intermediaries and its effect on blanket privacy for the purpose of this article.
Need for such rules
Over the past decade, the country has experienced a proliferation of social media, as a result, there has been a significant growth of concerns pertaining to misuse and abuse of social media for: spreading fake information; transmitting artificially edited images and videos of women in order to harass, intimidate, threaten; disrespecting religious beliefs or sentiments by transmitting abusive, defamatory remarks in order to spread violence, disharmony; carrying out financial frauds by the criminals and inducing people to become terrorists.
The Supreme Court in a suo-moto writ petition directed the Government of India to frame necessary guidelines to eliminate child pornography, rape and gangrape imageries, videos and sites in content hosting platforms and other applications. The Supreme Court in a case directed the Ministry of Electronics and Information Technology to appraise the timeline in respect of completing the process of notifying the new rules. The Ad-hoc committee of the Rajya Sabha gave recommendations to enable identification of the first originator of the contents in matters pertaining to pornography which had the worst effect on children and society.
Important definitions
Intermediary with respect to any particular electronic records, means any person who on behalf of another person receives, stores or transmits that record or provides any service with respect to that record as per section 2(w) of the IT Act. An intermediary also includes websites, apps and portals of social media networks, media sharing websites, blogs, online discussion forums and other such functionally similar intermediaries as per the ‘Code’.
Social Media Intermediary means an intermediary which primarily or solely enables online interaction between two or more users and allows them to create, upload, share, disseminate, modify or access information using its services.
Significant Social Media Intermediary (hereinafter ‘SSMI’) means a social media intermediary having a number of registered users in India above such threshold as notified by the Central Government as per rule 2(y) of the ‘Code’.
Key provisions impacting blanket privacy
Storage of Information
Restrictions have been imposed on intermediaries regarding hosting, storing or publishing any information that affects sovereignty, integrity, security of the State and its friendly relations with foreign states under clause (d) of Rule 4 of the ‘Code’. If any such information is hosted, stored or published, the intermediary has to remove or disable access to that information within thirty-six hours from receipt of the order of a competent court or the appropriate government under clause (b) of sub-section (3) of Section 79 of the IT Act.
Further, the intermediaries who have either received: an order from the competent court; or appropriate government under clause (d) of Rule 4 of the ‘Code’; or any complaint by any user, need to preserve such information and associated records for a period of one hundred and eighty days or more if required by the court or by Government as per clause (g) of rule 4 of the ‘Code’.
Collection of information
The intermediaries are also required: to collect information from a user for registration on the computer resource and also to retain his information for a period of one hundred and eighty days if the user has cancelled or withdrawn from such registration, as per clause (h) of rule 4 of the ‘Code’; to provide information under its control or possession, or any assistance to the Government agency who is lawfully authorised for investigative or protective or cyber security activities, for the purposes of verification of identity, or for the prevention, detection, investigation, or prosecution of offences under any law for the time being in force, or for cyber security incidents within seventy two hours as per clause (j) of rule 4.
Identification of the first originator
‘SSMI’ who are providing messaging services have to enable the identification of the first originator of that information on its computer resource, which can affect sovereignty, integrity, security of the state, friendly relations with foreign states, or public order, or offences relating to rape or child sexual abuse material which are punishable for a term not less than five years. This can only be done on receipt of the order of the competent court or an order passed under Section 69 of the Act by the Competent Authority as per the Information Technology (Procedure and Safeguards for interception, monitoring and decryption of information) Rules, 2009.
In complying to such order no ‘SSMI’ would be required to disclose the contents of any electronic message related to the first originator, or its related users. If the first originator of any information is found to be located outside India, the person who started spreading that information first in India would be the first originator as per clause (2) of rule 5.
Use of technology measures
‘SSMI’ have to deploy technology-based measures to identify acts or simulation pertaining to rape, child sexual abuse or conduct and to also identify that information which has been removed or whose access has been disabled previously. These measures need to be implemented in such a way that freedom of speech & expression, privacy of users is not affected.
User verification
‘SSMI’ are required to verify the accounts of the users who register for their services from India using an appropriate mechanism which will also include verification of active Indian mobile number and when a user successfully verifies their account, a visible mark of verification needs to be shown along with his name and such mark needs to be visible to all registered users. Information received from a user for verification purposes can’t be used for any other purpose unless the user gives its consent as per clause (7) of rule 5.
How these provisions impact privacy
First Originator
This rule clearly is going to have a major threat to the privacy of the users. The issue of traceability of originators of information on messaging platforms is also the subject of litigation before the Supreme Court in Antony Clement Rubin v. Union of India (T.C. Civil No.189 of 2020). This case originated as a PIL before the Madras High Court seeking linking of Aadhaar with social media accounts. However, during the course of hearings before the Madras High Court, the focus shifted to traceability of originators of information on end to end encrypted platforms such as WhatsApp and the case was later transferred to the Supreme Court. Messages sent from one person to another person on platforms like WhatsApp and Facebook are encrypted and use complex cryptographic functions. Now, if the data which is being transmitted over the internet is not protected, there is a possibility that it might get stolen or attacked by cyber hackers using various techniques and algorithms. Let us first understand cryptography.
Cryptography is the process of hiding or encrypting the data in such a manner that only the intended recipient gets to know what data has been transmitted to him/her after decrypting such data. Let us understand this with the help of the following figure:
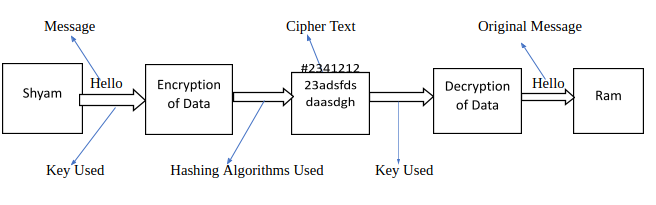 In the above example, Shyam is sending a message ‘Hello’ to Ram but see how it goes through a series of encryption and decryption algorithms before Ram actually receives the message in its original form. Here 2 keys are being used, if both the keys are same i.e. Public keys then it would be known as Symmetric Cryptography and if first key is public key which Shyam uses, and second key is private key which Ram has access to, would come under the meaning of Asymmetric Cryptography.
In the above example, Shyam is sending a message ‘Hello’ to Ram but see how it goes through a series of encryption and decryption algorithms before Ram actually receives the message in its original form. Here 2 keys are being used, if both the keys are same i.e. Public keys then it would be known as Symmetric Cryptography and if first key is public key which Shyam uses, and second key is private key which Ram has access to, would come under the meaning of Asymmetric Cryptography.
Cipher Text also known as ‘Unreadable Data’ is a string containing a mixture of numbers and alphabets containing hash value that could be as long as 30 digits. Various Hashing algorithms are used in order to calculate the cipher text. Now even if hackers are successful in stealing this information, they would only be able to obtain the Cipher text and not the original message. Cipher text can only be converted to its original message by using either the Public key which Shyam and Ram is having or through the private key which only Ram has access to. There is no other way through which Cipher text can be converted back to its original message. In this way, the whole information is protected. Most of the ‘SSMI’ use a mixture of Symmetric and Asymmetric cryptographic algorithms at different stages in order to enhance security.
Even though the rule of finding first originator states that contents of message of first originator or its associated users need not be disclosed but while finding the first originator, encryption algorithms will need to be broken. This means that the data will be exposed to higher risks of cyber hackers due to the vulnerabilities which will arise after removing certain security algorithms. As a result, the public faith in messaging platforms will be significantly reduced and there is potential for the breach of the fundamental right of speech of Indian citizens as well as blanket privacy.
Non-erasure of data
The requirement that data of those users who have withdrawn or cancelled their registration on a platform needs to be kept for a period of one hundred and eighty days seems to be in conflict with Article 17(1) of GDPR which talks about the ‘right to erasure’ or ‘right to be forgotten’. It poses a real threat to those users who have already cancelled or withdrawn their registration from a particular platform and this clause will need to evolve. In Subhranshu Rout @ Gugul vs. State Of Odisha , both the petitioner and the accused were classmates and loved each other. One day the accused went to the girl’s home and taking advantage of the fact that she was alone, he committed rape and recorded the whole episode in his mobile phone.
When the girl told her parents about the incident, he opened a facebook account in her name and uploaded all the objectionable photos from her account. Justice S.K. Panigrahi while addressing the case highlighted the significance of right to be forgotten and observed that under Indian laws strong penal action has been prescribed for rape but no mechanism has been made available with respect to the right of the victim to get the objectionable content deleted from the server of the Facebook. Social media platforms have really seen significant growth in such a number of cases where people’s right to privacy which are intricately linked to their right to get deleted permanently the objectionable content from servers of such social media platforms have been left unresolved.
However, similar issues have been dealt with in the European Union with the help of the General Data Protection Regulation (GDPR) which focuses mainly on the collection, processing and erasure of personal data. The matter pertaining to right to forget or right to erasure have been discussed in Recitals 65 and 66 in Article 17 of the GDPR which gives victims a right to erasure of such objectionable content after due diligence by the controller in an expeditious manner. Also, Article 5 of GDPR stipulates the fact that data controllers would need to take reasonable steps to erase personal data without undue delay, on being approached by such users whose personal data needs to be deleted. These provisions would only need to evolve over time as India clearly needs to move forward with a positive outlook and start giving importance to the blanket privacy of the users.
Assisting the government
The fact that an ‘SSMI’ needs to assist the government by providing information under its control or possession for verification of identity, for the prevention, detection, investigation or prosecution of offences within seventy-two hours will lead to a situation where government agencies would be using this rule for their own political benefits more often than not and thereby posing a threat to the privacy of its users. This is likely to impact blanket privacy in a negative manner.
Data retention
The requirement of storing records of users for a period of one hundred and eighty days appears to be excessive if we compare it to the Article 5(1) of general data protection regulation (GDPR). Though India is not having its own data privacy law at this point of time, but in future, data protection laws similar to GDPR needs to be formed as many countries have already incorporated GDPR as it is. Also, chances of data leaks or breach can’t be denied. This will have huge implications on blanket privacy.
Use of automated tools
The government is trying to project it as a compliance requirement but, indirectly an excessive power has been given to ‘SSMI’ for tracking of information, users will be under constant fear that even if they post anything on social media, that information is being tracked always. This would also create a challenge for ‘SSMI’ to strike a balance between complying with the lawful order while safeguarding the right to privacy of its users.
User verification
Verifying the users through Mobile Number and providing them a badge or mark alongside their name would definitely reduce cases where people create fake accounts in other’s name and then commit frauds by asking for money from the friends of that user. Asking for user’s consent for using the information provided by them for other purposes would definitely have a positive impact on blanket privacy as this is in line with Global Data Protection Regulation (GDPR) which is a data privacy regulation for the European people, but has an impact on various companies globally.
Conclusion
With the new Code, the government has tried to regulate the long pending issues of social media, but there are certain things that will only evolve with time. Intermediaries will now have more burden to fulfil the compliance requirements. Data over the internet has really become huge to manage, which will only keep on increasing as time goes by. With more countries adopting GDPR, year by year India should move with a positive outlook to safeguard the interests of the privacy rights of users. On some fronts, the code tries to follow some aspects of GDPR by putting intermediaries under compliance requirements such as disclosing information to users and asking for the consent of the users, but at the same time some of the provisions of the ‘Code’ poses a real threat to blanket privacy.
References
- https://www.youtube.com/watch?v=H0eqWuj84-0&feature=youtu.be – Live Press Conference
- https://www.mondaq.com/india/media-entertainment-law/1042234/new-rules-for-digital-media-platforms-and-intermediaries
- https://indiankanoon.org/doc/6266786/ – Orissa HC on Right to be Forgotten
- https://thewire.in/tech/explainer-how-the-new-it-rules-take-away-our-digital-rights
- https://gdpr-info.eu/art-5-gdpr/ -GDPR Article 5(1)
- https://gdpr-info.eu/art-17-gdpr/ -GDPR Article 17
- https://gdpr-info.eu/recitals/no-65/ – GDPR Recital 65
- https://gdpr-info.eu/recitals/no-66/ – GDPR Recital 66
Students of Lawsikho courses regularly produce writing assignments and work on practical exercises as a part of their coursework and develop themselves in real-life practical skill.
LawSikho has created a telegram group for exchanging legal knowledge, referrals and various opportunities. You can click on this link and join:
 Serato DJ Crack 2025Serato DJ PRO Crack
Serato DJ Crack 2025Serato DJ PRO Crack











 Allow notifications
Allow notifications


