This article is written by Shrikar Ventrapragada, pursuing Diploma in Cyber Law, FinTech Regulations, and Technology Contracts from LawSikho.
Table of Contents
Introduction
Undeniably, the internet is becoming the worldwide information infrastructure. With the advancement in the security mechanisms and development in the legal provisions, that exist to protect the network of computers which store the valuable data of its users.
Phishing attacks aim at the weakest links i.e., the users who freely provide their users with their data without proper vigilance and care. In layman’s terms, a phishing attack is an attempt to trick and fool users into leaking their private information. Every phishing attack includes some type of social engineering, the attackers’ disguises as a trusted entity such as an e-commerce website, the IRS, etc, but in reality, it is a phishing campaign, just to trick you in and to take the bait.
Once the user is duped into opening the phishing email or the email spoof, it leads them to another web link and eventually leads to installing malware which may cause leakage in the user’s sensitive information. Access to critical information at times leads to a ransomware attack, in which the attackers demand a ransom in exchange for a person’s critical information such as login IDs and passwords, bank details, Credit card info, PAN Number, etc.
WannaCry is an example of a ransomware attack, it exploited the vulnerability in the Windows SMB protocol, it has a self-propagating mechanism that enables it to spread itself into other machines. In 2017, WannaCry spread rapidly and affected 150 countries, damaging 230,000 computers and causing damage of approximately $4 billion. According to FBI reports, Phishing attacks were the most common type of Cybercrime in 2020.
The article talks about the types of phishing attacks and the legal implications of the same. The article also reflects on the defence mechanisms against such phishing attacks.
Types of phishing
-
Deceptive phishing
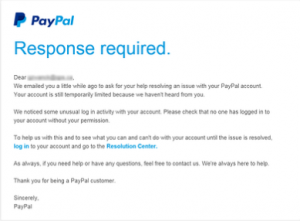
In this type of phishing, fraudsters create a fake domain that pretends to be the website of a genuine organization and send multiple requests with a sense of urgency to frighten the readers and lure them into the trap of the attackers. Here is how a malicious email may look like:
Source: https://www.phishing.org/phishing-examples
Deceptive phishing can be of various forms such as:
- Email spoof that contains legitimate links, only to disable the phishing protection filters.
- Shortened URLs that contain malicious software and become a bridge to their phishing campaigns.
- Altering the HTML attributes by changing the colour and other features to fool detection tools. Email filters recognize the identity of an organization by looking out for the HTML attributes. If the HTML attributes are modified, the whole email filters are disabled automatically.
- Using images instead of text, to avoid getting detected in the anti-phishing filters.
What can be the possible defence mechanism for such an attack?
The success of a deceptive phish hinges on how closely the attack email resembles a piece of official correspondence from the abused company. As a result, users should inspect all URLs carefully to see if they redirect to an unknown and/or suspicious website. They should also look out for generic salutations, grammar mistakes, and spelling errors scattered throughout the email.
-
Spear phishing
This is a type of phishing wherein the attackers aim at a particular target. Such a target can be a person or an organization as well. Fraudsters customize their phishing emails with the name of the target, their position, their place of work, phone number, and other details of the targeted person only to lure him into believing it to be true and that such a mail is in relevance to the target.
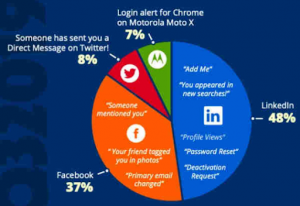
This type of phishing can commonly be seen in social media sites such as LinkedIn, wherein the whole bio-data of an individual is accessible to multiple data sources, which craft a spear-phishing email.
Source: https://static.wixstatic.com/media/file.jpg
Examples of spear phishing are:
- Hackers are increasingly using digital storage facilities such as DropBox, Google Drive, and other cloud services to house their malicious files and documents.
- Session or Cookie Hijacking: this is an issue when the attacker has the access to a user’s accounts and their critical information is sacrificed.
- Optimum utilization of social media to identify target individuals who can be easily boxed out and lured into.
What can be the possible defence mechanism for such an attack?
To protect against this type of scam, organizations should conduct ongoing employee security awareness training that, among other things, discourages users from publishing sensitive personal or corporate information on social media. Companies should also invest in solutions that analyze inbound emails for known malicious links/email attachments. This solution should be capable of picking up on indicators for both known malware and zero-day threats.
-
Executive phishing
There is a Nigerian criminal group known as the London Blue, which is known for gathering information on CFOs and other prominent employees of companies. Also known as Whaling, where attacks are directed specifically at prominent employees and senior executives, and other high-profile targets.
The content may be in the form of a customer complaint or a notice of summons and it shall be crafted in the interest of the person.
CEO fraud is the opposite of Whaling, as it involves a spoofed email, which is supposed to be from a senior executive to get other employees in an organization to perform a specific task, and it usually consists of sending money to an offshore account. There have been multiple instances of organizations losing hundreds of millions of dollars to such an attack.
What can be the possible defence mechanism for such an attack?
Whaling attacks work because executives often don’t participate in security awareness training with their employees. To counter the threats of CEO fraud and W-2 phishing, organizations should mandate that all company personnel, including the executives, participate in security awareness training on an ongoing basis. Organizations should also consider injecting multi-factor authentication (MFA) channels into their financial authorization processes so that no one can authorize payments via email alone.
-
Vishing
Vishing is the use of the telephone to facilitate a phishing attack. The fraudsters use an automated voice recording that makes false claims of random fraudulent activities on the target’s bank accounts or credit cards.
The fraudster portrays themselves as the real number of the bank or the institution they choose to showcase themselves as. From there, the victim is redirected to the call which is under the attackers, which asks them for their card numbers or account numbers to ‘resolve’ the claimed problem the target is facing (as claimed by the phishers).
The phishers use VoIP which is Voice over Internet Protocol to conduct phishing attacks.
There is a city named Jamtara in the state of Jharkhand, located in the Eastern region of India. It is known as the phishing capital of India. Between the brief period of 2015-2017, there were 14000 fake numbers recovered in this region. This district is known for its phone-call-related scams.
What can be the possible defence mechanism for such an attack?
To protect against vishing attacks, users should avoid answering calls from unknown phone numbers, never give out personal information over the phone and use a caller ID app.
-
Smishing
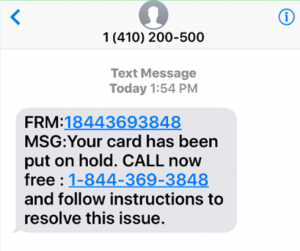
Smishing is the form of phishing wherein the fraudsters trick users by sending malicious text messages which contain websites links that are filled with malicious content.
Source: https://www.kratikal.com/blog/smishing-attack-a-growing-cyber-threat/
Opening these links triggers an automatic download of a phishing app that automatically installs ransomware in the device white permits remote access of the device from a remote unknown region. These messages involve provocative information about the user winning a lottery ticket or a smartphone or any random unknown gain to the user, which usually costs them a fortune in purchasing. The messages are strategically planned to ensure that the user is convinced to open the campaign that redirects them to the phished website.
There are also instances wherein the attacker pretends to be calling from customer service representatives and lures the users into handing them their data by helping them to contact the technical support team.
What can be the possible defence mechanism for such an attack?
Users can help defend against smishing attacks by researching unknown phone numbers thoroughly and by calling the company named in the messages if they have any doubts.
-
Pharming
Phishing attacks are known and users expect it beforehand and are hence prepared for it, hence most fraudsters are now using modern techniques of phishing.
Pharming attacks are the type of attack wherein cache poisoning is used as leverage against the domain name system (DNS). The internet can detect and thereby direct its users to a secured DNS server.
Now what a DNS does is, converts the alphabetical link of a website to a numerically formed IP address.
Example: www.google.com/ is formed into a numerical IP address.
Now in case of a pharming attack, the DNS server’s IP address is modified to that of the Phishing website, and the users have directed that website.
What can be the possible defence mechanism for such an attack?
To protect against pharming attacks, organizations should encourage employees to enter login credentials only on HTTPS-protected sites. Companies should also deploy anti-virus software on all corporate devices and implement virus database updates regularly. Finally, they should stay on top of security upgrades issued by a trusted Internet Service Provider (ISP).
How can phishing be prevented?
Phishing can be prevented by following the below mentioned simple techniques:
- Having a basic understanding of what phishing is, attackers often target the weakest links, not being the weak link is always an advantage to the user.
- Reading, before opening any links, apps, and emails, sometimes when the user reads a message, they can detect if it is a piece of genuine information or not.
- Getting free anti-phishing notifications, most web-browsers provide the facility to add an anti-phishing extension to the browser, this extension detects in case of a phishing possibility.
- Being sensible, with whom we provide our information. Being vigilant in providing information to unsecured sites is a very important step in being safe from a phishing scam. Looking out for the URL is also a small hack in identifying phishing, secured websites always have ‘https’ or a lock sign to the left of the URL.
- Keeping a track of your passwords and modifying them regularly.
- Updating an app or a service regularly not only helps us keep our data safe, but also ensures that past phishing attempts are erased and eradicated.
- Being aware of the pop-ups, pop-ups are the most common way for a phishing attack. When closing a pop-up, the users need to make sure that they close the whole tab and not select ‘close’ on the pop-up because at times the ‘close’ button has malicious content.
- Critically analyzing before providing our personal information. Before giving any personal information, the user should ask himself three questions, who am I providing the information to, why am I giving it, where is it going. The user needs to check the authenticity of the information, they need to verify it before handing over any personal data.
- Last, but the most important, user training, above all the given measures, the user needs to be aware of what they are getting into. Users need to be aware of how phishing scams happen and how to be safe from them.
Provisions for phishing under the Indian laws
Phishing is a fraud that is recognized as cybercrime and attracts many penal provisions of the Information Technology Act, 2000 (hereinafter referred to as ‘IT Act’). This act was amended in the year 2008, which added a few new provisions and solutions that give a scope to deal with the Phishing activity.
The sections which apply to phishing under the IT Act are:
- Section 43: If any person without the permission of the owner of the computer, computer system, computer network; accesses, downloads, introduces, disrupts, denies, or provides any assistance to other people can be held liable under this section.
- Section 66: If the accounts of a victim are compromised by the phisher, who does any act mentioned in section 43 of the IT act, shall be imprisoned for a term which may exceed up to three years or with a fine which may exceed up to five lakh rupees or both.
- Section 66A: Any person who sends any information which he knows to be false, but is sending it with the intention to damage a victim shall be punishable with the punishment given under section 66 of the IT act. In the case of Shreya Singhal vs. Union of India, the court held that online intermediaries would only be obligated to take down content on receiving an order from the courts or government authority.
- Section 66C: This provision prohibits the use of electronic signatures, passwords, and any other feature which is a unique identification of a person. Phishers disguise and portray themselves as the true owners of the accounts and perform fraudulent acts.
- Section 66D: The provision provides punishment for cheating by personating using communication devices or computer sources. Fraudsters use URLs that contain the link for a fake website of banks and organizations and personate themselves as the bank or the financial institution.
- Section 81: This provision consists of a non-obstante clause i.e., the provisions under this act shall affect notwithstanding anything inconsistent, and also contained in any other act for the time being in force.
The obstinate clause overrides the effect of the provisions of the IT Act over the other acts such as the Indian Penal Code.
All the provisions of the IT Act, 2000 which are relevant to the phishing scams are however made bailable under Section 77B of the IT Act (Amendments 2008). This is obviously because of the uncertainty as to who the real criminal is. There is always a translucent screen in front of the phisher which hides their identity and there may be cases wherein the wrong person is convicted for a crime that they have never committed, hence the reason for the offense to be made bailable.
Furthermore, as per the Indian Penal Code, Phishing can also be held liable under Cheating (Section 415), Mischief (Section 425), Forgery (Section 464), and Abetment (Section 107).
Conclusion
It is evident that cybercrimes are a major threat to the technology-growing world. As the technology intensifies so should the laws related to such cybercrimes, in this context phishing. There is no such overarching national law in India that oversees the collection and usage of personal data in India.
A few relevant laws which govern the protection of data in India include the Information technology act (amendment) 2008, Information Technology (Reasonable security practices and procedures and sensitive personal data or information) Rules, 2011. i.e., the sensitive personal data or information) Rules 2011. On the other hand, the Reserve Bank of India has issued a directive on the storage of Payment System Data, the purpose of this directive is to ensure that the RBI can monitor payment by accessing all payments data. The RBI regulates the payment aggregators and payment gateways.
The United Kingdom has a dedicated Fraud Act 2006 which handles the misuse of technology, other such provisions under the legislation of the UK are the computer Misuse Act 1990 and Network and information systems regulations 2018. The UK is also a member of the Convention on Cybercrime.
The first international treaty which highlighted cybercrime was the ‘convention on cybercrime’ also known as the ‘Budapest convention on cybercrime’. This treaty was drawn by the members of the Council of Europe.
It can be concluded that the Indian laws which govern phishing are similar to that of the laws of the EU and UK. But unfortunately, there are major gaps in the Indian laws. The SPDI rules are restricted and only apply to the personal data of individuals. The government agencies and non-profit organizations are immune from the SPDI compliances. The regulations set up by RBI are only restricted to the financial sectors and are hence limited in application. There must be sufficient safeguards to ensure the anonymized data cannot be re-identified, and no harm can be caused to the original data principal. Therefore, a law to regulate non-personal data is important to disincentivize cybercrime and ensure that businesses safeguard their resources.
References
- https://csgtechnologies.net/2021/05/
- https://www.thesslstore.com/blog/10-types-of-phishing-attacks-and-phishing-scams/
- https://www.itgovernance.eu/blog/en/the-5-most-common-types-of-phishing-attack
- http://www.supremecourtcases.com/index2.php?option=com_content&itemid=5&do_pdf=1&id=19b497
- https://www.lexology.com/library/detail.aspx?g=a6e35288-c18d-433f-83c1-4525d348d6cf
Students of Lawsikho courses regularly produce writing assignments and work on practical exercises as a part of their coursework and develop themselves in real-life practical skills.
LawSikho has created a telegram group for exchanging legal knowledge, referrals, and various opportunities. You can click on this link and join:
 Serato DJ Crack 2025Serato DJ PRO Crack
Serato DJ Crack 2025Serato DJ PRO Crack











 Allow notifications
Allow notifications


