This article is written by Rishabh Mishra, pursuing a Diploma in Cyber Law, Fintech Regulations, and Technology Contracts from LawSikho.com.
Table of Contents
Introduction
Roscoe Pound propounded the doctrine of social engineering, under the Sociological School of Jurisprudence. He defined the law as “Law is social engineering which means a balance between the competing interests in society,” in which applied science is used for resolving individual and social problems. The introduction of the doctrine of social engineering was done with an aim to achieve balance in the society, by creating an efficient structure for the society, to provide satisfaction for maximum desires with least waste. Pound connected engineering with a lawyer’s job, to achieve the purpose of building a possible scientific structure for the society. Individual interest, public interest and social interest are three heads that are made to achieve the task of social engineering.
Social engineering has a different terminology in the cyber world and has no relation to doctrine of Social Engineering propounded by Roscoe Pound. In the cyber world social engineering is a technique or art to manipulate any person to give up his/her personal information such as any access to a system, bank accounts or any other valuables. This article attempts to cover various types of social engineering attacks, how these different attacks operate, which important part is played by social engineering attacks and laws governing the prevention of social engineering attacks.
Types of social engineering
Before understanding the types of social engineering attacks and their manner of operation, there are stages which are followed by every attacker irrespective of its type, that must be discussed. This technique of social engineering basically exploits human errors by installing software in the computer which gives them access to other personal data and data. Under this technique manipulation is based on the user’s behavior, the attacker basically tries to understand the user’s action to successfully influence him with intent to deceive. This technique requires four steps and they are:
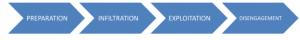
At the stage of preparation, the attacker gathers all the information of his target. Then, he works on creation of trust with the target through interaction and other means with intent to infiltrate his personal area. After creating trust and discovering the weakness, attackers start to exploit the victim to progress in his conduct. Once the target does an act intended by the attacker, the attacker disengages himself from the whole transaction. There are various types of social engineering attacks but these types are not limited to phishing, baiting, diversion theft, pretexting, quid pro quo, scareware, tailgating, water holing and 419/Nigerian Prince/advance fee scam.These types are explained below:
1. Phishing
It is one of the most common forms of attack. Under this type, an attacker can influence the user to share his personal data and pretend as if it is a trusted person or institution. These attacks generally take place through links or attachments of e-mail. There are various types of phishing such as:
a. Spam
Under this type, attacks are on large users and non-personalised in nature.
b.Spear or whaling
Under this type, attacks are very much personalized in nature and for targeted people only.
c. Angler
Under this type, attackers use customer service accounts on social media and imitate to be a trusted company. By intercepting the conversation of the user and the company, they manipulate users to divert their conversation to personal space attackers where they proceed with being deceived.
d. BEC
BEC is an abbreviation of business email compromise. The email is sent to an employee from the attacker, who purports to be a senior of such an employee.
e. Smishing
Smishing or SMS Phishing is conducted through text messages or mobile apps by sending compromised links to the user.
f. URL Phishing
The attacker sends compromised links through email, social media messages or online ads and influences people to access such websites.
g. Search-engine Phishing
The attacker tries to put compromised links in the top results of search engines. These links may appear in the form of paid ads or may use other legitimate methods for manipulation.
h. Tabnabbing/reverse tabnabbing
The attacker alters the unwatched browser tabs with compromised content. It is pertinent to mention that types of phishing are not limited to the types mentioned above. Scammers may use different methods of phishing through communications to deceive users for filling their pockets.
2. Baiting
As the name suggests, the attacker basically uses one’s natural curiosity to explore more by manipulating that person through free or exclusive offers. Generally a malware is sent by an attacker to the target user. One of the methods of baiting is the distribution of infected devices such as leaving USBs at public places, such as libraries or parking lots. Another method is sending emails containing details of free content.
3. Diversion theft
The attacker intercepts the offline deliveries of products and manipulates them to send it to erroneous recipients. The attacker manipulates the user to send his personal or confidential information or data to an erroneous recipient.
4. Pretexting
The attacker creates a fake identity and impersonates a legitimate entity or person. They create a whole background story of their condition or work and with their proactive efforts influence users till they satisfy them with their legitimacy.
5. Quid Pro Quo
It is a latin term which means one thing for another thing. Attackers offer rewards in exchange for any information which you may give to him but are deceived at the end after giving information.
6. Scareware
It is a malware which is used by an attacker to scare users through alarming messages, pop-ups that say you have a virus in your computer or your account has been compromised. Thus, they push users to buy, or download free, cyber security software which compromises the personal details of the user.
7. Tailgating
The attacker influences an authorized person to give access to him in a restricted area. This is basically a physical security breach to gain access to a secure or restricted area.
8. Water holding
The attackers try to find vulnerabilities in the website and use them for their benefits. Generally, users of popular websites are targeted for accessing information at mass.
9. 419/Nigerian Prince/Advance Fee Scam
As this scam originated in Nigeria and Section 419 of Nigerian Criminal Code penalises this practice and this is the reason it is known as 419 or Nigerian Prince. Scammers manipulate users to share their bank details or pay an advance fee or amount to transfer money out of their country.
Importance of social engineering
As evident from the various types of social engineering attacks and various other methods which are not covered above such as DNS spoofing, peer to peer network attacks etc., plays an important role for securing devices. Wherever there is a threat there is a need for security, thus, social engineering attacks indirectly promote a sense for security of devices. Precautions are also as important as security as precautions help you to spot these attacks and in order to spot these attacks at institutional and individual levels, one may follow the tips suggested below:
- There should be effective training of all employees.
- Creation of security awareness.
- Cyber security software must be in use and updated regularly.
- Must be able to identify social engineering attacks.
- Use only trusted websites for software download.
- Must not act hastily to share credentials.
- Must check the background of websites before making any kind of transaction.
The above are some of the precautionary measures which must be adopted by persons to secure themselves from social engineering attacks. These attacks are a threat to the society by affecting the economic structure of its members. The only important part social engineering plays is that it creates a sense of security in the cyber world, otherwise it has only a negative part to play, as these attacks cannot be eliminated because of unpredicted innovations in the cyber world but they can surely be mitigated by being aware.
Laws governing social engineering attacks
Social engineering : intention of deceiving someone
Social engineering is basically cheating which is defined under Section 415 of Indian Penal Code, 1860 (in short IPC). It says when any person with intent to deceive another person dishonestly or fraudulently induces any person to deliver any property or retain any property or makes such person to do or omits to do any act which he would not have done unless deceived, thus, thereby causes harm or may cause harm to such person in body, mind, reputation or property.
Backing deception to gain property
In all the types of social engineering attacks, one common factor is deception to gain property or infiltration. These types are basically methods of cyber deception and for these deception practices various fake documents are also used such as bonds, agreements, Trademarks of established brands etc along with impersonation of identity. Forging of documents attracts the penal provision which is defined under Section 463 of IPC, it says preparation of false documents which shall include electronic records with intent to commit fraud to any person or public at large to cause any damage or injury, frauds such as claiming title or support any claim or cause any person to part with property or to enter into any express or implied contracts are covered by the definition.
Preparing false documents with dishonest and fraudulent intentions
Section 464 of IPC also defines how false documents are prepared. False documents are made with dishonest and fraudulent intentions which may contain seal, sign, execution of document, transmission of electronic record or its part, affixing electronic signature, makes any mark denoting authenticity of document or made in the name of fictitious person pretending it to be real person. Cheating, impersonation and forgery are penalised in various sections depending upon the facts and circumstances of the case.
Throwing light upon the provisions under the Information Technology Act, 2000
So far as Information Technology Act, 2000 is concerned, Sections 65 to 66D are concerned with offences related to impersonation and cheating. Other sections such as Section 68, 69, 70, and 71 are concerned with non-compliance with government directions and notifications and Section 71 is concerned with misrepresentation and suppression of material facts for obtaining license, which in other terms stand for cheating and forgery because it is made with intent to deceive. Section 72 is concerned with data leaks whereas, Section 72A is concerned with all types of social engineering attacks because it penalises such person who without the consent of another person or violating lawful contract gained access to personal information with the intent of causing him wrongful loss or wrongful gain and Section 73 and 74 is concerned with forgery of electronic signature certificates.
It is pertinent to mention that Section 75 of the Information Technology Act, 2000 is concerned with extra territorial operation of the Act because it says any computer, computer system or computer network source is located in India and is used for offences outside India then such person, irrespective of its nationality, shall be liable under IT Act, 2000 for contravention of its provision. This simply means if any person hacks a computer source and uses it for wrongful gains or wrongful loss to any person then such person shall be liable in India. In the same paraphernalia, Section 4 of IPC also mandates extra territorial operation of IPC and specifically covers any act of a person, who is outside India, targets any computer resource in India. This aspect also covers social engineering attacks. Provisions under IPC such as Section 417 to Section 420 for cheating and Section 465 to Section 477A for forgery and provisions under IT Act have different penalties for different offences with minimum penalty of three months and maximum penalty of life imprisonment under various sections of both the laws.
Steps taken by Central Government for awareness of cyber security
There are some of the steps taken by the Central Government for prevention and mitigation of cyber security incidents. They are as follows:
- Establishment of National Critical Information Infrastructure Protection Centre (NCIIPC) for protection of critical information infrastructure in the country under Section 70A of Information Technology Act.
- Cyber security incidents must be mandatorily reported to CERT-In by all organizations providing digital services in an expeditious manner. CERT-In is established under Information Technology (The Indian Computer Emergency Response Team and Manner of performing Functions and Duties) Rules, 2014 made under Section 87 and 70B of the Information Technology Act, 2000.
- Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre) has been launched for providing detection of malicious programmes and free tools to remove such programmes.
- Issue of alerts and advisories regarding cyber threats and counter-measures by CERT-In.
- Issue of guidelines for Chief Information Security Officers (CISOs) regarding their key roles and responsibilities for securing applications / infrastructure and compliance.
- Provision for audit of the government websites and applications prior to their hosting, and thereafter at regular intervals.
- Empanelment of security auditing organisations to support and audit implementation of Information Security Best Practices.
- Formulation of Crisis Management Plan for countering cyber attacks and cyber terrorism.
- Conducting cyber security mock drills and exercises regularly to enable assessment of cyber security posture and preparedness of organizations in Government and critical sectors.
- Conducting regular training programmes for network/system administrators and Chief Information Security Officers (CISOs) of Government and critical sector organisations regarding securing the IT infrastructure and mitigating cyber attacks.
Conclusion
Both the terminologies i.e. “Doctrine of Social Engineering” and “Social Engineering in cyber world” mean poles apart and field of operation, thus, have no common ground. One can be used to create balance in the society with scientific means and the other is to create ruckus by cheating. The only thing which could be covered under doctrine of social engineering is that under the head of social interest the modern terminology of social engineering needs to be balanced for safe and secured transactions in the society as use of this technique shall result in various law and order situation which will have economic offences at the center and also affects other heads under the doctrine as well.
Social engineering attacks have only one important part to play for society i.e. creation of a sense of security through threats and irrespective of the type of social engineering attacks penal provision under IT Act squarely covers all of them because of the inclusive nature of provision. But, most of the penal provisions of IT Act co-relate with provisions of IPC in their own area of operation. Although all these provisions under IT Act and IPC cannot be said to be preventive in nature as they only operate after attempt or commission. Thus, the government had taken various steps and initiatives to mitigate the threats to cyber security. One thing is clear from the perusal of cyber laws and initiatives taken by the government towards cyber security is that all the efforts of the government are directed to mitigate the threat and not to eliminate them because they understand the dynamic nature of the world of cyberspace and new threats may arise any moment.
References
- https://www.lawnotes4u.in/2020/04/social-engineering-by-roscoe-pound-sociological-school.html
- https://blog.ipleaders.in/all-about-social-engineering/
- https://www.kaspersky.com/resource-center/definitions/what-is-social-engineering
- https://www.itgovernance.co.uk/social-engineering-attacks
- https://blog.eccouncil.org/social-engineering-and-the-role-it-plays-in-cybersecurity/
- https://pib.gov.in/Pressreleaseshare.aspx?PRID=1579226
Students of LawSikho courses regularly produce writing assignments and work on practical exercises as a part of their coursework and develop themselves in real-life practical skills.
LawSikho has created a telegram group for exchanging legal knowledge, referrals, and various opportunities. You can click on this link and join:
 Serato DJ Crack 2025Serato DJ PRO Crack
Serato DJ Crack 2025Serato DJ PRO Crack









 Allow notifications
Allow notifications


